4 Principles of encryption
4.3 The components of a symmetric key system
I shall now explain the components of a symmetric key system in more detail.
A block cipher operates on groups of bits – typically groups of 64. If the final block of the plaintext message is shorter than 64 bits, it is padded with some regular pattern of 1s and 0s to make a complete block. Block ciphers encrypt each block independently, so the plaintext does not have to be processed in a sequential manner. This means that as well as allowing parallel processing for faster throughput, a block cipher also enables specific portions of the message (e.g. specific records in a database) to be extracted and manipulated. A block of plaintext will always encrypt to the same block of ciphertext provided that the same algorithm and key are used.
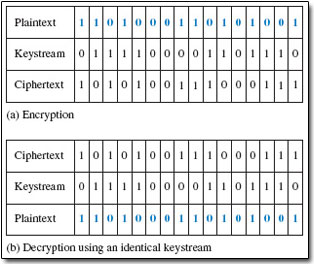
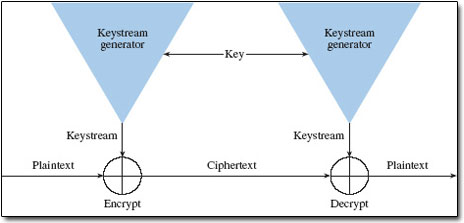
A stream cipher generally operates on one bit of plaintext at a time, although some stream ciphers operate on bytes. A component called a keystream generator generates a sequence of bits, usually known as a keystream. In the simplest form of stream cipher, a modulo-2 adder (exclusive-OR or XOR gate) combines each bit in the plaintext with each bit in the keystream to produce the ciphertext. At the receiving end, another modulo-2 adder combines the ciphertext with the keystream to recover the plaintext. This is illustrated in Figure 6. The encryption of a unit of plain text is dependent on its position in the data stream, so identical units of plaintext will not always encrypt to identical units of ciphertext when using the same algorithm and key.
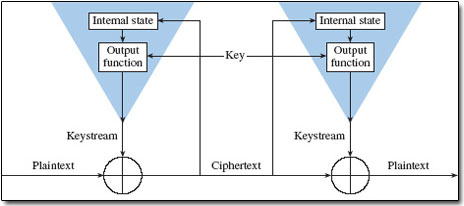
Stream ciphers can be classified as either synchronous or self-synchronising. In a synchronous stream cipher, depicted in Figure 7, the keystream output is a function of a key, and is generated independently of the plaintext and the ciphertext. A single bit error in the ciphertext will result in only a single bit error in the decrypted plaintext – a useful property when the transmission error rate is high.
In a self-synchronising cipher, depicted in Figure 8, the keystream is a function of the key and several bits of the cipher output. Because the keystream outputs depend on the previous n bits of the plaintext or the ciphertext, the encryption and decryption keystream generators are automatically synchronised after n bits. However, a single bit error in the ciphertext results in an error burst with a length dependent on the number of cipher output bits used to compute the keystream.
A selection of some symmetric key systems used in popular software products is given in Table 2.
Table 2: Examples of commercial symmetric key systems
| Algorithm | Description |
| DES (Data Encryption Standard) | A block cipher with a 56-bit key. Adopted in 1977 by the US National Security Agency (NSA) as the US Federal standard, it has been one of the most widely used encryption algorithms but, as computers have become more powerful, it is now considered to have become too weak. |
| Triple-DES (or 3DES) | A variant of DES developed to increase its security. It has several forms; each operates on a block three times using the DES algorithm, thus effectively increasing the key length. Some variants can use three different keys, the same key three times, or use an encryption–decryption–encryption mode. |
| IDEA(International Data Encryption Algorithm) | A block cipher with a 128-bit key published in 1990. It encrypts data faster than DES and is considered to be a more secure algorithm. |
| Blowfish | A compact and simple block cipher with a variable-length key of up to 448 bits. |
| RC2 (Rivest cipher no. 2) | A block cipher with a variable-length key of up to 2048 bits. The details of the algorithm used have not been officially published. |
| RC4 (Rivest cipher no. 4) | A stream cipher with a variable-length key of up to 2048 bits. |
Often the key length for RC2 and RC4 is limited to 40 bits because of the US export approval process. A shorter key reduces the strength of an encryption algorithm.