9 Access control
9.4 Packet-filtering router
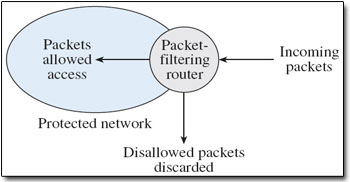
A packet-filtering router either blocks or passes packets presented to it according to a set of filtering rules. Figure 14 shows this arrangement.
Filtering rules are based on various features of the service or protocols involved, including:
- the packet header information, e.g. IP source and destination addresses
- the encapsulated protocol being used, e.g. TCP or UDP, ICMP or IP tunnel (see Box 4 below)
- the transport layer source and destination ports
- the ICMP message type
- the incoming and outgoing interfaces for the packet.
UDP (user datagram protocol) is a transport layer protocol in the internet reference model. It is used for traffic that does not need the services of a TCP connection. ICMP (internet control message protocol) is used to communicate problems from routers and hosts in the network. It supports, for example, the widely used PING command referred to in Section 3.6.
Box 4: IP tunnel
In IP tunnel an extra IP header is added to a packet to avoid revealing the originating source and final destination IP addresses when a message is being sent across an intermediate network. This idea of concealment of header details by tunnelling is employed in some important security protocols that have been developed specifically for use in IP networks over the internet.
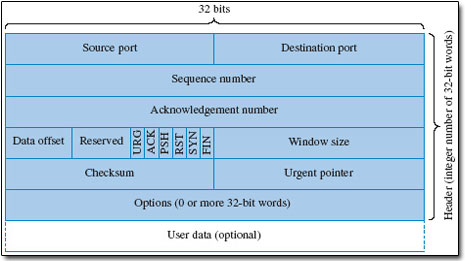
The choice of rules and the way in which they are implemented will allow a router to admit or bar specific types of user traffic. Services that may be called up by users at their computers are generally identified in terms of TCP or UDP port numbers. Figure 15 shows where TCP port numbers are identified in the header and the box on TCP port numbers explains briefly the concept of TCP ports.
Box 5: TCP port numbers
TCP is a connection-oriented protocol and provides services by creating end points called sockets at client and server machines. A socket uses the IP address of the host and a 16-bit port number. (A port is sometimes referred to as a transport service access point.) Port numbers below 1024 are reserved for standard services and are referred to as well-known ports.
For example, Telnet is an application protocol associated with the TCP/IP family. It enables a user at one computer to log in to another computer, issue commands to the operating system, and run programs. A Telnet server will listen for remote connections on TCP port 23, while an email service based on another application protocol, SMTP (simple mail transfer protocol), will listen for incoming connections on TCP port 25.
The Internet Assigned Numbers Authority (IANA) has a list of well-known ports on its website: www.iana.org/assignments/port-numbers
From the description in the box, Telnet presents a significant security risk in terms of its ability to exercise remote control of a workstation, server or other network device. However, Telnet can be disallowed by including its TCP port number in the filtering rules. Given that a TCP port number specifies a type of service and an IP address specifies a host address, you should be able to see how combinations of the two can be used to restrict access to certain services to certain hosts. Consider this further by attempting SAQ 12.
SAQ 12
How could a packet-filtering router:
- restrict incoming traffic from a specified external network?
- restrict access to a Telnet service to selected hosts behind the firewall?
- combat an attempt by an outside source to masquerade as an internal host?
- The router could disallow all packets from the specified network by referring to the relevant IP addresses in the filtering rules.
- In the filtering rules TCP port 23 could be disallowed for all hosts except those with certain internal IP addresses.
- An external attack could be based on knowledge of one of the target network's internal IP addresses. However, a packet arriving at a network interface from an external circuit, but having an internal source IP address, would be highly suspect. This could be reflected in the packet-filtering rules by specifying that, for all interfaces from external circuits, packets presenting source addresses that are internal network IP addresses would be barred. This type of attack is termed ‘IP address spoofing’.
There are many types of attack that can be resisted using packet-filtering rules, but I shall consider just one other as an example.
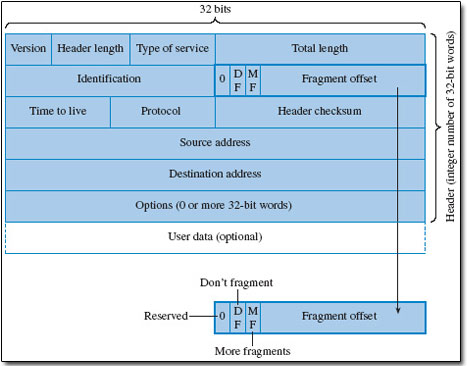
Figure 16 shows the structure of an IPv4 packet. The fragment offset field and the three flag bits that precede it in the packet header allow an IP packet to be split into two or more fragments, if it would otherwise exceed the maximum size set by the lower layer frame limit. However, this feature could be misused in a number of ways. For example, a fragment could be forced to be so small that the encapsulated packet header information would be split between fragments. Using this tactic, an attacker could circumvent filtering rules that checked the header information of encapsulated packets (e.g. the port identities of an encapsulated TCP segment as in Figure 15) only in the first fragment that is received.
SAQ 13
Figure 15 defines the format of a TCP segment that is to be transported using IP. What would be the minimum number of bytes that should be included in a fragmented IP packet to ensure that the TCP port identification was included?
The IP header shown in Figure 16 includes 5 rows of 32 bits, assuming no options are present. This equates to 20 bytes. The TCP destination port in Figure 15 is at the end of the first row of 32 bits, so another 4 bytes would ensure that both TCP ports were included. Therefore a minimum of 24 bytes would be required.
A certain way to avoid a restricted service being accessed through the misuse of IP fragmentation would be to reject any IP packet in which fragmentation was allowed. In practice, when fragmentation is allowed, packet-filtering routers are usually set to reject IP fragments that are less than 20 bytes greater than the IP header length.
Defining the rules under which packets are filtered demands a wide knowledge of internet service types. Filtering rules need to be detailed and can become complex. When packets are filtered using complex rules, the time for each packet to be processed by the router may increase significantly and degrade system performance. When traffic must be restricted because of its likely topic content, a packet-filtering approach that works on the basis of addresses (at the IP and TCP levels) will not be able to meet requirements. A higher layer approach is needed and this can be provided by the application level gateways that I shall describe next.
Despite the limitations of packet-filtering routers, they are widely deployed as they are economical and can be implemented on standard routers, although additional software may need to be installed. Users behind a packet-filtering firewall generally find the degree of restriction involved acceptable and relatively unobtrusive.