3 Threats to communication networks
3.5 Potential network vulnerabilities
Whatever the form of attack, it is first necessary to gain some form of access to the target network or network component. In this section I shall take a brief look at a hypothetical network to see where an attacker may achieve this in the absence of appropriate defence measures.
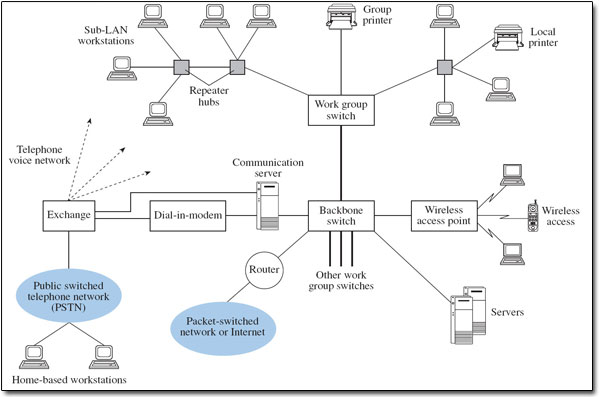
Figure 3 shows the arrangement of a typical local area network (LAN), in which repeater hubs provide interconnections between workstations for a group of users (a work group), with different work groups being interconnected through backbone links and having access to the public switched telephone network (PSTN) and a packet-switched network. Repeater hubs are also used to refresh the transmitted signal to compensate for the attenuation caused by the transmission medium. I shall use Figure 3 to explore the potential for security breaches in a basic network.
Typically, the LAN will be Ethernet based, operating on the broadcast principle, whereby each packet (or strictly frame) is presented to all workstations on the local segment, but is normally accepted and read only by the intended receiving station. (Segment in this context refers to part of a local area network.) A broadcast environment is advantageous to someone attempting to carry out either a passive or an active attack locally. Switches that separate work groups on a LAN incorporate a bridge function, and bridges learn where to send packets by noting the source addresses of packets they receive and recording this information in a forwarding table. The contents of the forwarding table then determine on which port on the switch packets will be sent. An attacker could corrupt entries in forwarding tables by modifying the source address information of incoming packets presented to a bridge. Future packets could then be forwarded to inappropriate parts of the network as a result.
SAQ 3
How would you categorise this form of attack?
Referring to Figure 2 (see Section 3.2), the modification of the source address corresponds to a message modification attack. This could then lead to a masquerade/fabrication attack if the purpose was for the attacker to receive messages intended for another computer. Alternatively, the misdirection of messages could result in a denial-of-service attack.
Routers also have forwarding tables that may be vulnerable to attack. However, they are configured in a different way from switches and bridges, depending on the security policies applied to the network. In some networks human network managers load forwarding tables that may remain relatively unchanged over some time. In larger networks, routing algorithms may update forwarding tables automatically to reflect current network conditions. The policy may be to route packets along a least-cost path, where the criterion for least cost may be, for example, path length, likely congestion levels or error rate. As routers share information they hold with neighbouring routers, any breach of one router's tables could affect several other routers. Any interference could compromise the delivery of packets to their intended destination and cause abnormal loading in networks, leading to denial of service. Routing tables or policies can be changed legitimately by, for example, network management systems, and this highlights the need for the management systems themselves to be protected against manipulation by intruders.
Returning to Figure 3, some organisations need to provide dial-in facilities for employees located away from the workplace. Dial-in access may present further opportunities for attack, and measures to protect this vulnerability will need to be considered. A wireless access point is also indicated, providing access for several wireless workstations to the wired LAN. Reports of security breaches on wireless LANs are widespread at the time of writing (2003), giving rise to the term ‘drive-by hacking’, although many instances have occurred quite simply because basic security features have not been activated. As a result, all the attacks on the LAN that I have described so far can be performed by someone who does not even have physical access to the site, but could be on the street nearby, for example in a parked car.
Some places on a LAN are particularly vulnerable. For example, connections to all internal data and voice communication services would be brought together in a wiring cabinet for patching across the various cable runs and for connecting to one or more external networks. An intruder would find this a convenient point for tapping into selected circuits or installing eavesdropping equipment, so mechanical locks are essential here.