5 Implementing encryption in networks
5.1 Overview
Confidentiality between two communicating nodes is achieved by using an appropriate encryption scheme: data is encrypted at the sending node and decrypted at the receiving node. Encryption will also protect the traffic between the two nodes from eavesdropping to some extent. However, for encryption to be used effectively in networks, it is necessary to define what will be encrypted, where this takes place in the network, and the layers that are involved in a reference model.
Activity 8
What are the implications of applying encryption to whole protocol data units including the headers at any particular layer of a reference model?
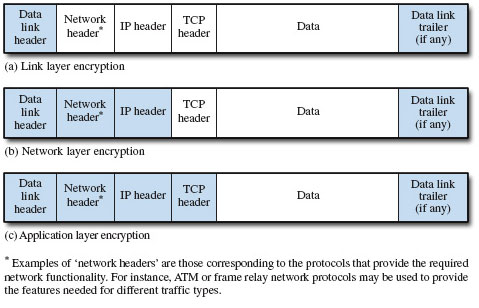
The protocol data unit headers include addressing information; if this is obscured, it will prevent the effective routing of protocol data units to their destination. In a packet-switched environment each switch must be able to read the address information in the packet headers. Encrypting all the data including the headers of each packet at the sending node would render the switches at intermediate nodes unable to read the source or destination address without first decrypting the data.
The implementation of encryption in packet-switched networks must ensure that essential addressing information can be accessed by the relevant network devices such as switches, bridges and routers. Encryption is broadly termed link layer encryption or end-to-end encryption depending on whether it is applied and re-applied at each end of each link in a communication path, or whether it is applied over the whole path between end systems. It is useful to identify the various implementations of encryption with the appropriate OSI layer, as indicated in Figure 9.
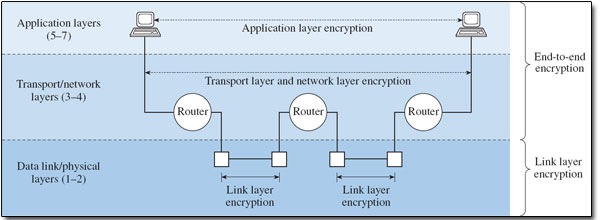
Figure 9: Encryption in relation to the protocol layers (Source: based on King and Newson, 1999, p. 104)
End-to-end encryption is implemented at or above layer 3, the network layer of the OSI reference model, while link layer encryption is applied at the data link and physical layers. When encryption is applied at the transport or network layers, end-to-end refers to hosts identified by IP (internet protocol) addresses and, in the case of TCP (transmission control protocol) connections, port numbers. In the context of application layer encryption, however, end-to-end is more correctly interpreted as process-to-process. Figure 10 identifies the extent of encryption (unshaded areas) applied at each layer.