4 Principles of encryption
4.2 An overview of symmetric key systems
We can think of symmetric key systems as sharing a single secret key between the two communicating entities – this key is used for both encryption and decryption. (In practice, the encryption and decryption keys are often different but it is relatively straightforward to calculate one key from the other.) It is common to refer to these two entities as Alice and Bob because this simplifies the descriptions of the transactions, but you should be aware that these entities are just as likely to be software applications or hardware devices as individuals.
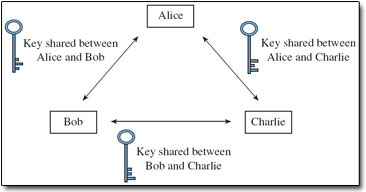
Symmetric key systems rely on using some secure method whereby Alice and Bob can first agree on a secret key that is known only to them. When Alice wants to send a private message to some other entity, say Charlie, another secret key must first be shared. If Bob then wishes to communicate privately with Charlie himself, he and Charlie require a separate secret key to share. Figure 5 is a graphical representation of the keys Alice, Bob and Charlie would each need if they were to send private messages to each other. As you can see from this, for a group of three separate entities to send each other private messages, three separate shared keys are required.
SAQ 4
Derive a formula for the number of shared keys needed in a system of n communicating entities.
Each entity in the network of n entities requires a separate key to use for communications with every other entity in the network, so the number of keys required by each entity is:
n − 1
But each entity shares a key with another entity, so the number of shared keys for each entity is:
(n − 1)/2
In a system of n communicating entities the number of shared keys required is:
n(n − 1)/2
SAQ 5
How many shared keys are required for a company of 50 employees who all need to communicate securely with each other? How many shared keys would be needed if the company doubles in size?
50 people would require (50 x 49)/2 = 1225 shared secret keys.
100 people would require (100 × 99)/2 = 4950 shared secret keys.